Your InnovationOS is the single source of truth for everything innovation. It is your home for innovation. It is thus important that you bring everyone on board. Read more on how to do it.
Read here more about:
1. Invite new users with local accounts
2. Authenticate and create new users with SSO
4. Role & Workspace Assignment via SSO
5. Populate user attributes via SSO
Invite new users with local accounts
To invite users individually, click on your username in the left bottom corner [1], and then go to the Organization Settings [2] or directly to Users & Invitations.

When you enter the tab "Users & Invitations" in your organization settings [1], you will find first a list of all users of your system [2].
To invite a user, find the button at the bottom right page of the screen [3]. By clicking "Invite User", a pop-up opens where you can enter the email address, the workspace(s) you want to invite the user to, and the role(s) you want to give to the user. Once done, click Invite user [5].
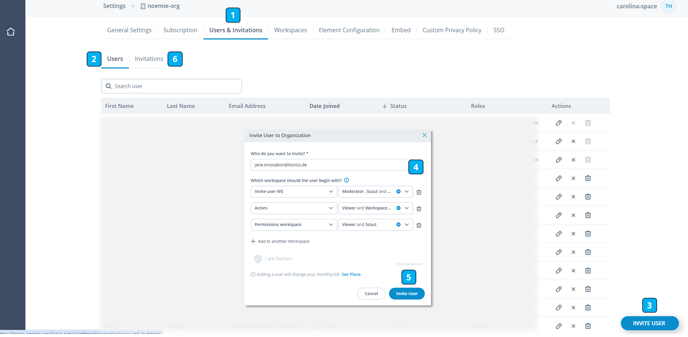
Please note that an invitation is valid for 7 days.
Please note that you can at max assign 5 user roles per workspace.
Please note that after a user has accepted the invite and logged in to the system for the first time, the user will get access to all public workspaces with the default role assigned. That also means that you only need to add a user to one public workspace during the invitation and only if he/she is not also invited to a private workspace or if you want to provide a different than the default role.
To see the status of the invitations, navigate to the "Invitations" tab [6] next to the "Users" tab [2]. Here, you will find an overview of all invited users (with a pending or expired invitation). The list contains the email address, invitation date, status, and a deletion action.
If you - as a Workspace Administrator - want to correct the role assignment later, navigate to the respective workspace settings and adjust the role given. Also, if you want to make a user an organization admin, you can do this after the user has logged in the first time.
Please note that the "Invite User" button does not appear when you have SSO enabled. Via SSO, every authenticated user from your active directory can directly log in to the system with their company credentials.
If you want to learn more about user management in general, please read this article.
Authenticate and create new users with SSO
Single Sign-On (SSO) allows users to access ITONICS using their corporate credentials via a SAML Identity Provider (IdP). Once SSO is activated, users gain access by visiting the system URL and authenticating through the SSO login.
User login flow
- User navigates to the ITONICS login page.
- Click the SSO login button (label is configurable during setup, e.g., “Log in with Azure” or “Use Company Login”)
- The user is redirected to your organization's Identity Provider (e.g., Azure AD, ADFS, OneLogin).
- Upon successful authentication:
- A user account is created with the role Member.
- Attributes imported: Email, First Name, Last Name.
- User is directed to a default public workspace.
Note: Access to private workspaces must be granted manually after the user's initial login or workspace allocation is configurable via Role & workspace assignments via SSO.
SSO configuration steps
Important: Attribute mappings must be entered before metadata can be fetched. Use placeholder values initially, then update them after metadata retrieval.
Go to Settings > SSO. Execute the following configuration steps:
- Title & Label: Set a Title for your IDP and define the Label for the SSO Log in Button. This label will be displayed on the Login Page. (1)
- Attribute Mapping (Placeholders): Before metadata can be fetched, input temporary values (2):
- Email: placeholder-email
- First Name: placeholder-firstname
- Last Name: placeholder-lastname
- Metadata Configuration: Choose the Metadata Configuration Type and upload a Metadata URL or a Metadata XML File Content. (3) You get the Metadata from your Active Directory. For instance, if you use Azure you can retrieve the Metadata from the SAML Certificates section in the respective Enterprise Application. The URL should look as follows: https://login.microsoftonline.com/{tenant-id}/federationmetadata/2007-06/federationmetadata.xml?appid={app-id}.
- Save the applied configuration (4)
- Based on your applied configuration – the IDP Configuration Information are generated (5)
- Your IT Team has to import the metadata to the Active Directory Federation Services (ADFS). Continue with the next step only once this is done!
- Attribute Mapping (6): Replace the placeholders from above. Map the attributes from your identity provider with the user attributes in ITONICS. Use the fully-qualified URIs provided by your IDP (e.g. "http://schemas.xmlsoap.org/ws/2005/05/identity/claims/givenname" instead of just "givenname"), which you can obtain from the metadata XML.
- Once you've completed the configuration, click Apply Changes to save your organization's SSO settings. (7)
- Enable SSO for your organization via the slider in the bottom-left corner. (8)
- You can also decide if you still want to allow Default Login with standard login credentials. (9) SSO needs to enabled first to activate the toggle.
- If you want to add another IDP you can do so by clicking on the +Add IDP button. (10) You can add up to three IDPs.
- For Azure users:
- Multiple Microsoft Entra IDs can be connected as separate IDPs if required.
- Each Entra ID requires a unique Metadata URL.
- A distinct login button will be displayed for each Entra ID
- For Azure users:
Role & workspace assignments via SSO
Automatically manage user roles and workspace memberships by leveraging your organization’s SSO (Single Sign-On) setup. By mapping specific attributes from your SAML configuration to roles and workspaces in ITONICS, you can ensure that every user gets the correct level of access from the moment they log in.
How It Works
-
Add a Claim Value for the Organization:
- In the configuration screen, locate the Claim Attribute field.
- Input the claim attribute received from your Identity Provider (IdP). This value serves as the key for mapping to your ITONICS organization roles.
-
Map Claim Values to Organization Role:
- In the Claim Values input field, enter the specific claim value that corresponds to the user’s profile.
- Select the appropriate organization role that should be assigned when the claim value is detected.
-
Assign Workspace Roles:
- Use the same approach to map claim values to roles for one or multiple workspaces within your organization.
- This step ensures that users are automatically granted the correct permissions in the designated workspaces based on their SSO attributes.

Populate user profile attributes via SSO
Enhance user profiles with automatically populated data from your SSO or Identity Provider. These additional fields can be used for future functionality, such as permissions management, group assignments, or custom automation.
How to Configure Dynamic Attribute Mapping
-
Click on "Add Attribute":
- Under the Dynamic Attribute Mapping subtitle on the User Profile Attributes configuration page, click the Add Attribute button to start the mapping process.
-
Select the IDP Field:
- In the configuration form, locate the field where you can specify the IDP (Identity Provider) Field.
- Enter the claim attribute that your IdP sends. For example:
http://schemas.xmlsoap.org/ws/2005/05/identity/claims/department
-
Map to a User Attribute:
- Next, select an existing user attribute or create a new one that should be updated with the value received from the IDP Field.
- This mapping ensures that the corresponding field on the user profile is automatically filled and updated upon login.

Changing a user's role
Once you have invited a user, you can still further change the roles per workspace or make any user the admin of your Innovation OS.
To change a role into a system admin role on the organizational level, navigate to the tab "Users & Invitations" on the organizational settings page. Find the user that you want to make an application administrator, click on the pen icon, and assign the admin role.

If you want to change a user's specific role in a workspace, navigate to the workspace tab on the organizational settings page. Here, you will find all your workspaces. Find the respective workspace, click the pen icon, and you will land on the workspace-specific settings page.

Navigate to the Users tab, search for the respective user, and click the pen icon. Now, you can assign him/her another role.